Bgroho Insights
Your daily source for news, tips, and inspiration.
Behind the Screens: Navigating Anonymity in Crypto Platforms
Uncover the secrets of staying anonymous on crypto platforms! Join us as we navigate the hidden world behind digital transactions.
Understanding Anonymity: How Crypto Platforms Protect Your Identity
In today's digital age, maintaining anonymity has become more crucial than ever, especially when it comes to financial transactions. Cryptocurrency platforms are at the forefront of this movement, employing advanced technologies to safeguard users' identities. By utilizing decentralized networks and blockchain technology, these platforms ensure that your personal information remains private. Additionally, many platforms allow users to transact without revealing their real names, adding an extra layer of protection against data breaches or identity theft.
Crypto platforms employ various methods to enhance user anonymity. For instance, they might use cryptographic techniques that mask the transaction details, or implement features like mixing services that obscure the origin of funds. Some platforms also encourage the use of privacy-focused coins, which are specifically designed to enhance confidentiality. As the discussion around digital privacy continues to evolve, understanding these mechanisms becomes essential for anyone looking to navigate the world of cryptocurrency while maintaining their anonymity.
Counter-Strike is a highly popular first-person shooter game that pits teams of terrorists against counter-terrorists in various objective-based scenarios. Players engage in intense, strategic gameplay that requires teamwork, quick reflexes, and tactical planning. For gamers looking to enhance their experience, a useful resource is the cryptocasino.com promo code, which can offer exciting bonuses.
The Pros and Cons of Anonymity in Cryptocurrency Transactions
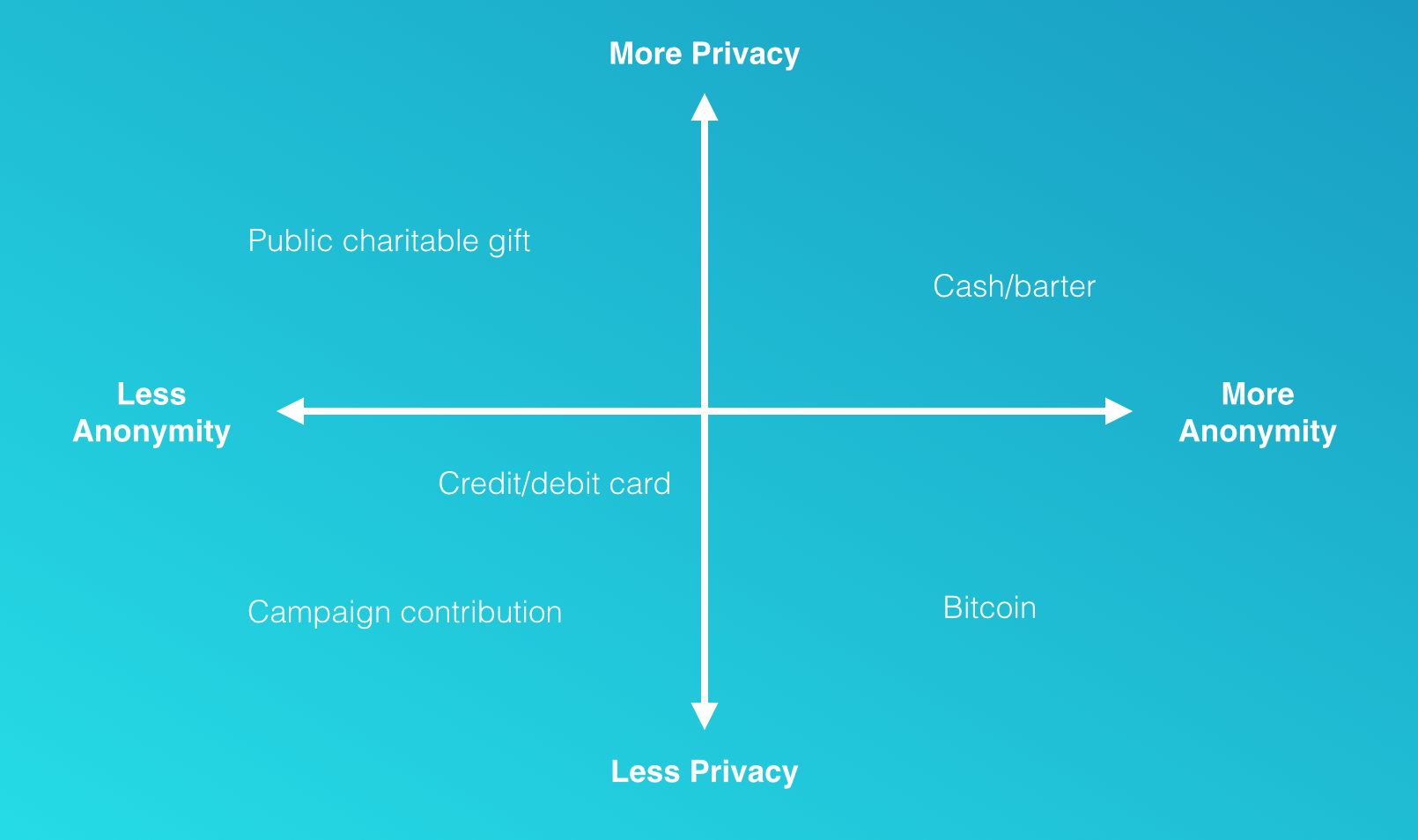
Anonymity in cryptocurrency transactions offers significant advantages, particularly in enhancing privacy for users. Many individuals appreciate the ability to transact without revealing their personal information, allowing them to maintain a level of financial privacy that is often difficult to achieve in traditional banking systems. This feature can promote financial freedom, enabling users to engage in transactions without fear of surveillance or censorship. Furthermore, the intrinsic nature of cryptocurrencies like Bitcoin and Monero encourages users to explore global markets without the restrictions typically imposed by governments or financial institutions. However, this aspect of anonymity can be a double-edged sword.
On the flip side, the anonymity provided by certain cryptocurrencies has raised concerns about illicit activities, including money laundering, tax evasion, and funding of criminal enterprises. This shadowy side can deter legitimate users and prompt regulatory scrutiny that might lead to stricter regulations impacting the overall industry. As governments around the world seek to impose regulations, the balance between privacy rights and regulatory compliance becomes increasingly thorny. As users weigh the pros and cons of anonymity, understanding these dynamics is essential for informed decision-making in the evolving landscape of cryptocurrency transactions.
What You Need to Know About KYC Regulations and Privacy in Crypto
KYC regulations, or Know Your Customer regulations, are designed to prevent illegal activities such as money laundering and fraud in the cryptocurrency space. These regulations require cryptocurrency exchanges and other service providers to collect and verify the identity of their users before allowing them to trade or conduct transactions. While these measures are necessary for ensuring compliance with financial laws, they raise significant concerns regarding privacy. Users often worry that sharing personal information could lead to data breaches or misuse of their data.
Understanding the balance between KYC regulations and privacy is crucial for cryptocurrency users. On one hand, compliance with KYC is essential for a sustainable crypto ecosystem, helping to build trust and legitimacy. On the other hand, users should be aware of their rights regarding personal data protection. It is important to choose reputable exchanges that prioritize both compliance and user privacy, Implementing measures such as end-to-end encryption and minimal data collection can help maintain user confidentiality while adhering to necessary regulations.